Tag: data protection
-
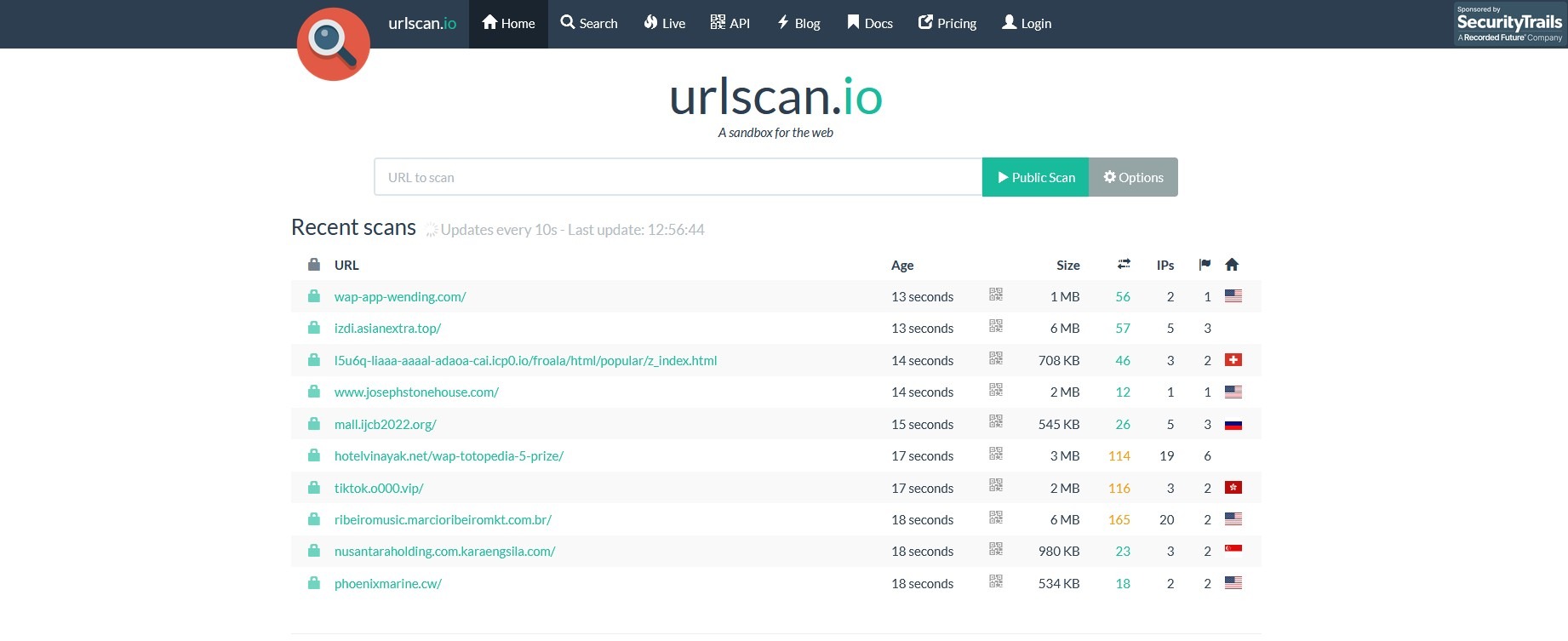
Mastering URL Analysis with urlscan.io: Your Essential Guide to Phishing Detection and Web Security
In today’s digital landscape, malicious URLs pose one of the most significant threats to organizational security and individual privacy. With cybercriminals constantly evolving their tactics, the ability to quickly and accurately analyze suspicious links has become paramount for both cybersecurity professionals and general staff members. Enter urlscan.io, a powerful web service that transforms URL analysis…
-
Critical Clickjacking Attack Exposes Password Manager Vulnerabilities: What SMBs Need to Know
A sophisticated Clickjacking attack has been discovered that can compromise password managers and steal sensitive credentials, putting small and medium-sized businesses (SMBs) at unprecedented risk. This alarming cybersecurity threat demonstrates how attackers can manipulate trusted security tools, turning our most fundamental protection mechanisms against us. For cybersecurity professionals and business owners alike, understanding this attack…
-
Revolutionizing Cybersecurity: How SOAR Tools Are Transforming Security Operations Automation
In today’s rapidly evolving threat landscape, cybersecurity teams face an unprecedented challenge: managing an ever-increasing volume of security alerts while maintaining the speed and accuracy required to protect critical assets. The traditional manual approach to security operations has become unsustainable, with security analysts drowning in alert fatigue and organizations struggling to respond to threats in…
-

Top Cybersecurity APT Groups in 2025: Advanced Threat Actors and Their Dangerous TTPs
As we navigate through 2025, the cybersecurity landscape continues to evolve at an unprecedented pace, with Advanced Persistent Threat (APT) groups becoming increasingly sophisticated in their tactics, techniques, and procedures (TTPs). These state-sponsored and financially motivated threat actors represent the pinnacle of cyber warfare capabilities, targeting critical infrastructure, government entities, and private organizations worldwide. Understanding…
-

DOJ Seizes $2.8M in Crypto from Zeppelin Ransomware: A Game-Changer for Cybersecurity
In a groundbreaking operation that sends shockwaves through the cybercriminal underworld, the U.S. Department of Justice has successfully seized $2.8 million in cryptocurrency from operators of the notorious Zeppelin ransomware group. This landmark case represents a significant victory in the ongoing battle against ransomware attacks and demonstrates the evolving capabilities of law enforcement agencies in…
-

The Rise of AI-Driven Cyber Attacks: How Artificial Intelligence is Revolutionizing Advanced Persistent Threats
The cybersecurity landscape is experiencing a seismic shift as artificial intelligence transforms from a defensive tool into a weapon of unprecedented sophistication. AI-driven cyber attacks are emerging as the next frontier in digital warfare, enabling threat actors to launch campaigns with a level of precision, adaptability, and scale previously unimaginable. As organizations worldwide grapple with…
